Enterprise-Grade Security
Bank-level encryption, comprehensive access controls, and compliance frameworks designed for the legal industry's strictest requirements.
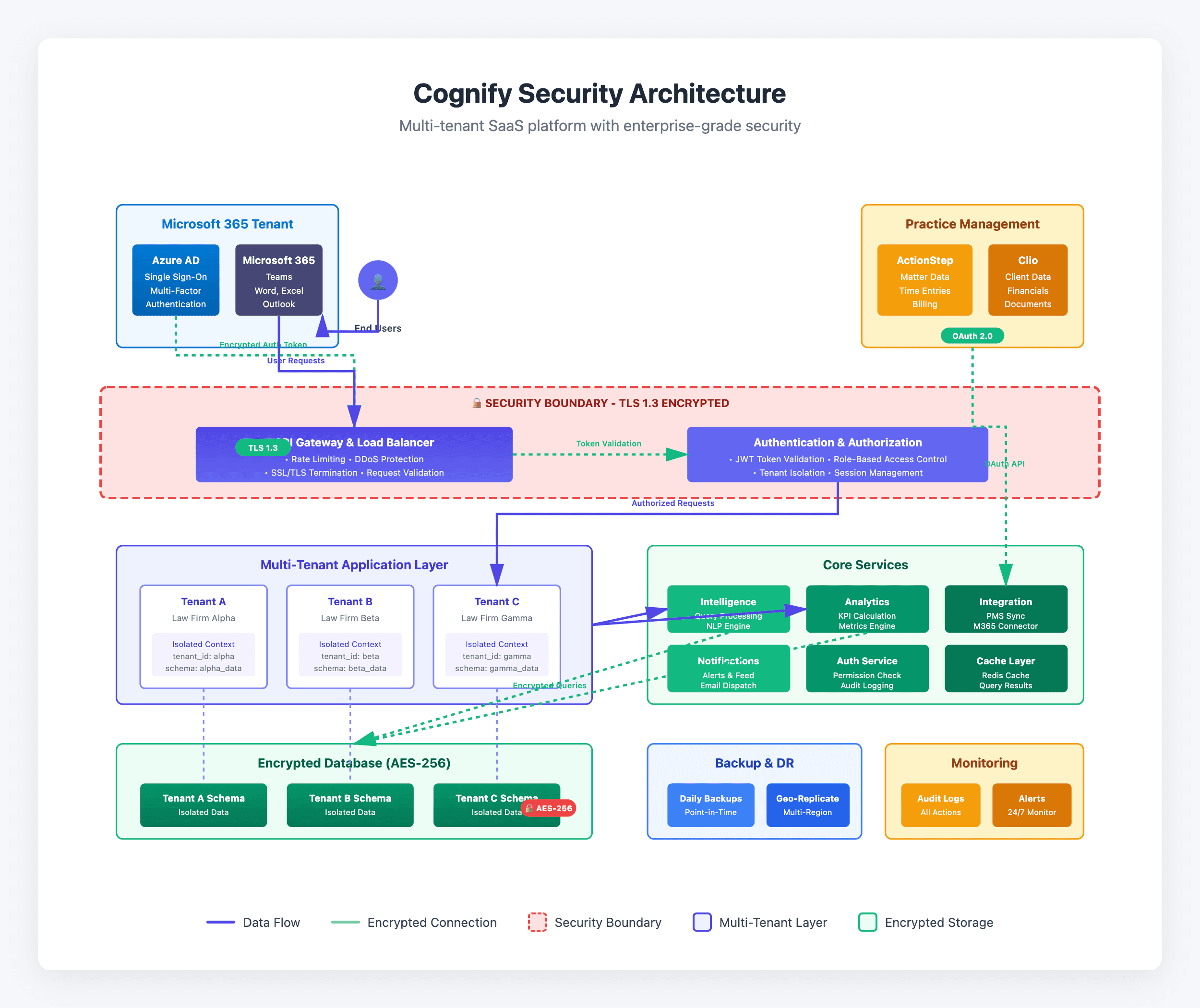
How We Protect Your Data
Multiple layers of security protecting your most sensitive client and matter information at every point.
Data Encryption
Your data is encrypted at every stage using industry-standard protocols that meet or exceed regulatory requirements.
- ✓AES-256 encryption for data at rest
- ✓TLS 1.3 for data in transit
- ✓Encrypted database storage
- ✓Encrypted backups
- ✓Key rotation and management
Access Controls
Granular role-based permissions ensure users only access data appropriate to their role and responsibilities.
- ✓Role-based access control (RBAC)
- ✓Matter-level permissions
- ✓Chinese wall support
- ✓Multi-factor authentication (MFA)
- ✓Single sign-on (SSO) via Azure AD
Multi-Tenant Isolation
Complete data separation between firms with dedicated partitions and zero data sharing.
- ✓Logical data partitioning per tenant
- ✓Isolated database schemas
- ✓Separate encryption keys per tenant
- ✓Independent backup and recovery
- ✓Zero cross-tenant data access
Audit Logging
Comprehensive logging of all system activity for compliance, investigation, and accountability.
- ✓All data access logged
- ✓User authentication events
- ✓Configuration changes tracked
- ✓Immutable audit trail
- ✓Log retention: 7 years
Backup & Recovery
Automated backups with rapid recovery capabilities ensure your data is never lost.
- ✓Automated daily backups
- ✓Point-in-time recovery
- ✓Geographic redundancy
- ✓Encrypted backup storage
- ✓Tested disaster recovery procedures
Infrastructure Security
Built on enterprise cloud infrastructure with proven security and reliability.
- ✓Hosted on AWS/Azure
- ✓DDoS protection
- ✓Web application firewall (WAF)
- ✓Network intrusion detection
- ✓Regular security patching
Meeting Regulatory Requirements
Cognify is designed to meet the compliance needs of law firms handling sensitive client data.
GDPR
ActiveFull compliance with EU General Data Protection Regulation including data portability, right to erasure, and privacy by design.
SOC 2 Type II
In ProgressCurrently undergoing SOC 2 Type II audit covering security, availability, processing integrity, confidentiality, and privacy. Expected completion Q2 2025.
ISO 27001
Roadmap 2025International standard for information security management systems. Certification planned for Q4 2025 as we scale operations.
Our Data Commitments
Clear, transparent policies on how we handle, store, and protect your firm's data.
What We Collect
Practice Management Data
Matter information, time entries, invoices, client records, and financial transactions required to provide intelligence services.
Usage Analytics
Anonymized usage patterns to improve product performance and user experience. Never shared outside your firm.
Authentication Data
User credentials and session information managed through Microsoft Azure AD integration.
What We Don't Do
No Data Sharing
Your data is never shared with other firms, third parties, or used for any purpose beyond providing services to you.
No Training on Your Data
We do not use your firm's data to train AI models or improve services for other customers.
No Vendor Lock-In
Complete data export capabilities. You own your data and can leave with it at any time.
Data Residency
UK & EU Options
Data can be stored in UK or EU data centers to meet jurisdictional requirements and data sovereignty concerns.
Custom Requirements
Enterprise clients can specify data residency requirements during implementation based on regulatory needs.
Data Retention
Active Subscription
Your data is retained and backed up continuously throughout your active subscription period.
Post-Cancellation
Data remains accessible for 90 days after cancellation. After 90 days, all data is permanently deleted unless you request earlier deletion.
Secure by Design
Our platform architecture prioritizes security and data isolation at every layer.
Defense in Depth
Multiple layers of security controls ensure that a single point of failure doesn't compromise your data.
Zero Trust Model
Every request is authenticated and authorized regardless of source. No implicit trust within the network.
Least Privilege Access
Users and services are granted only the minimum permissions necessary to perform their functions.
Security Incident Management
Clear procedures for detecting, responding to, and communicating about security events.
Detection & Classification
24/7 monitoring systems detect potential security events. Incidents are classified by severity: Critical, High, Medium, Low.
Immediate Response
Security team is alerted immediately. Critical incidents trigger emergency response procedures within 15 minutes.
Customer Notification
Affected customers are notified within 72 hours for data breach incidents, within 24 hours for service disruption.
Remediation & Prevention
Root cause analysis, system hardening, and updated procedures to prevent recurrence. Post-incident reports provided to affected customers.
Security Contact: Report security concerns to security@cognifylegal.com
Download Our Security Whitepaper
Comprehensive technical documentation covering our security architecture, compliance frameworks, and data protection practices.
Download Whitepaper (PDF)Questions About Security?
Our team is happy to discuss your specific security and compliance requirements in detail.